
Client authentication is similar to server authentication except that the telnet server requests a certificate from the client to verify that the client is who it claims to be. The certificate must be an X.509 certificate and signed by a certificate authority (CA) trusted by the server. You can only use client authentication when a server requests a certificate from a client. Not all servers support client authentication, including the Host On-Demand Redirector. The later versions of the IBM Communications Servers (CS/NT, CS/AIX, etc.) all support client authentication.
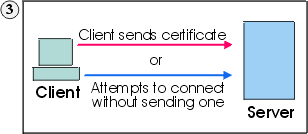
When a server requests a certificate, the client has the option to send a certificate or attempt to connect without it. The server allows the connection if the client's certificate can be trusted. When a client attempts to connect without a certificate, the server might give the client access but at a lower security level.
 |
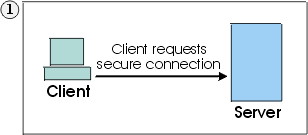
Client sends a request for an SSL session to Server. |
 |
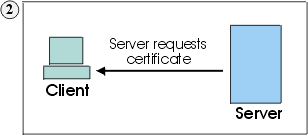
Client receives Server's certificate and checks its list of trusted CAs. Since Server's certificate is signed by a trusted CA, Client accepts the certificate. Server asks Client for a certificate that will identify the Client. |
 |
Client sends a certificate or tries to establish a session without one. |
 |
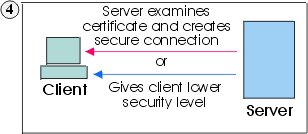
If Client sends a certificate, Server checks its list of trusted certificates. If the Client can be trusted, the secure session is established. If Client does not send a certificate, Server establishes a secure connection at a lower level of security. |
To configure client authentication:
When a certificate expires, follow the renewal procedures specified by the CA for that certificate.